Mastering Google Dorking: Unveiling the Secrets of Advanced Search Techniques
Explore the world of Google Dorking, from basic search operators to advanced filtering techniques, and learn how to uncover hidden information on the web.
What is Google Dorking?
Google Dorking, also known as Google Hacking, refers to using advanced search techniques on Google (or other search engines) to find specific information that is not easily accessible through normal queries. By utilizing special search strings (called Google dorks), you can apply operators like site:, filetype:, and intitle: to filter and refine search results. This can sometimes unintentionally expose sensitive information, vulnerabilities, or files that were never meant to be publicly available.
Real-World Applications
- Bug Bounty Hunting: Finding vulnerabilities like open directories or misconfigured security settings.
- OSINT: Gathering public data about individuals or companies.
- Cybersecurity Audits: Identifying unprotected files or sensitive information that may be publicly accessible due to misconfigura
Example: Searching for “Tesla”
In a basic Google search for “Tesla,” you see a variety of results related to the company, its cars, news, and more:
 This shows a standard Google search result page for the term “Tesla.”
This shows a standard Google search result page for the term “Tesla.”
Narrowing Down Results with Google Dorking
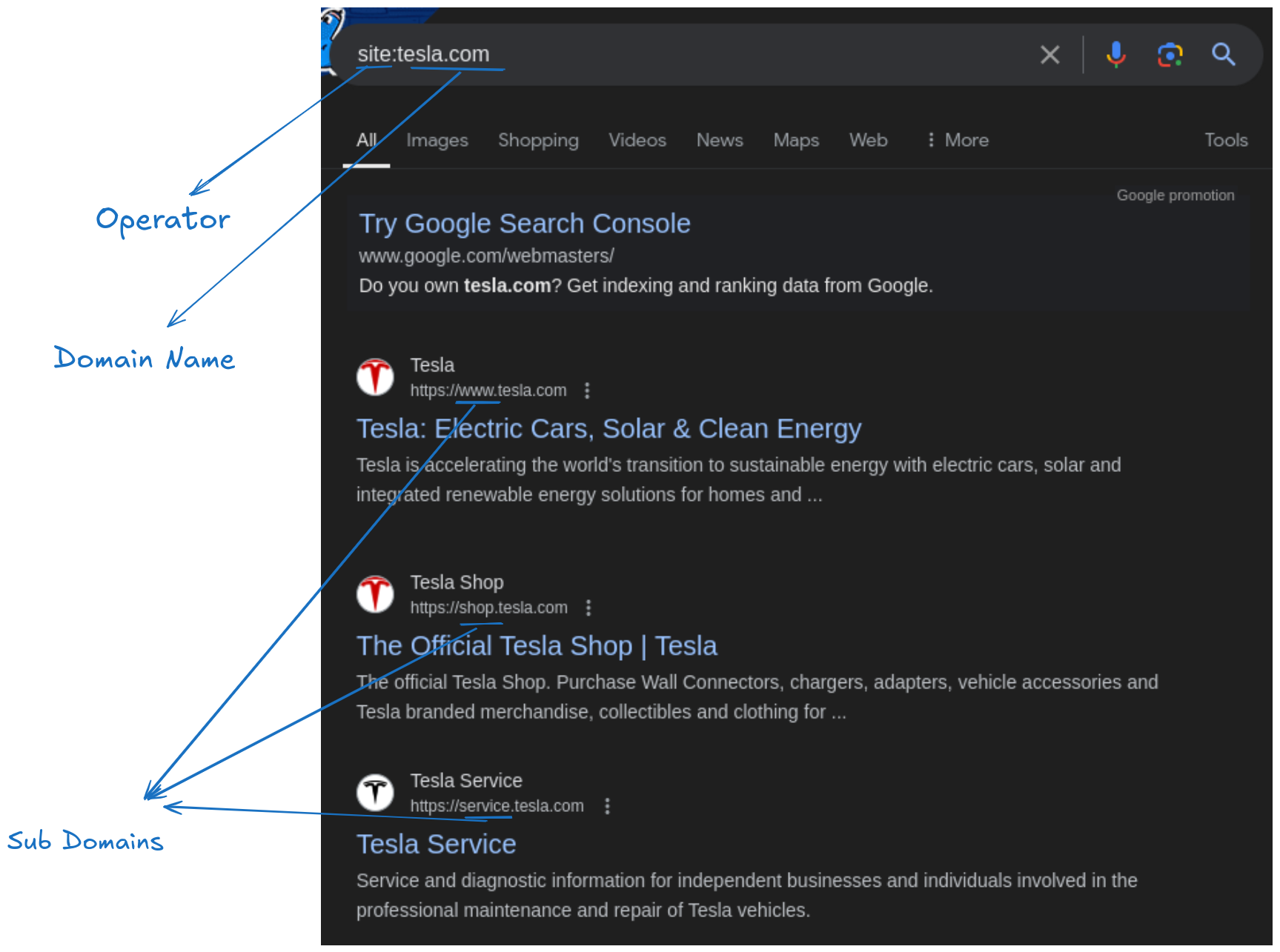
However, if you only want to view results that belong to Tesla’s official domain, you can use the site: operator to focus on a specific domain.
To do this, simply use the search string:
1
site:tesla.com
Here’s what it looks like:
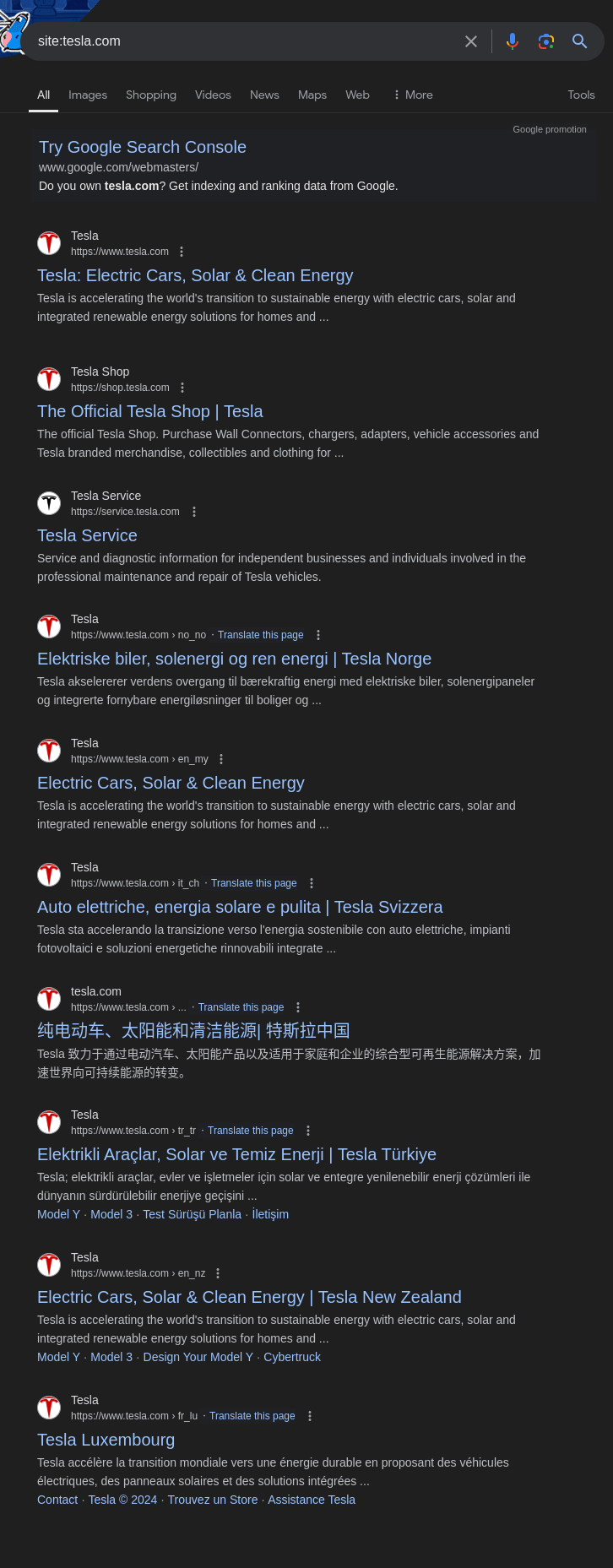
This filtered search displays only pages from tesla.com, effectively removing unrelated results from the search.
It looks like you’re diving deeper into using Google Dorking by refining search results further, specifically excluding subdomains. Here’s how you can structure that section in your presentation:
Let’s Deep Dive Into It
In some cases, you might want to exclude specific subdomains from your search results. For example, if you don’t want to see results from shop.tesla.com, you can modify the query to exclude that subdomain.
Excluding Subdomains from Results
You can use the - operator to remove certain terms from the search. For instance, to exclude the shop subdomain of Tesla, the search string would look like this:
1
site:tesla.com -shop
Here’s what happens:
Initial search without filtering subdomains like “shop”
Now, after applying the exclusion:
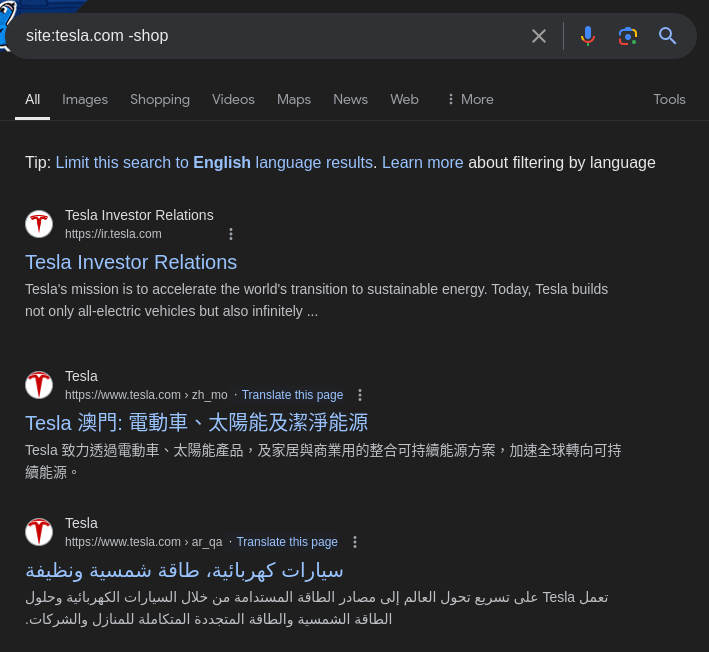
As you can see, the “shop” subdomain results have been excluded from the search.
Explanation:
site:tesla.com— Limits the results to the main Tesla domain and its subdomains.-shop— Excludes any results that contain the word “shop,” effectively removing shop.tesla.com from the results.
This technique is useful when you want to narrow down the results by removing irrelevant sections of a site, helping you focus on specific content.
Operators
Google Dorking leverages a variety of powerful search operators that allow you to filter and refine search results with precision. These operators provide control over how Google interprets and retrieves results, enabling you to uncover hidden data or focus on specific aspects of web pages.
Using Quotation Marks for Precise Searches
In Google Dorking, you can use quotation marks ("") to search for exact phrases or words in the same order, ensuring more precise results. This is especially useful when you want to find pages containing specific text combinations or when exact matches are necessary.
How to Use Quotation Marks
To search for an exact phrase, place it within quotation marks:
1
"exact phrase"
Example By using the query:
1
site:.com intitle:"index of"
You can filter for pages across .com domains where the title exactly matches “index of”, often indicating exposed file directories or unprotected file structures on the web.
Using the intitle: Operator
The intitle: operator in Google Dorking is a powerful tool that lets you search for web pages containing a specific word or phrase within the title of the page. The title refers to the text within the <title> HTML tag, which appears in both the browser tab and search engine results.
How to Use intitle:
To target pages with a specific word in the title, you can structure your query as follows:
1
intitle:query
For example:
1
intitle:login
This query will return web pages that include the word login in their title.
Example: Searching for Login Pages
If you want to find login pages across various websites, you can combine the intitle: operator with a domain filter like so:
1
site:.com intitle:login
This query will search for login pages from websites with a .com domain. Here’s an example of how it works:
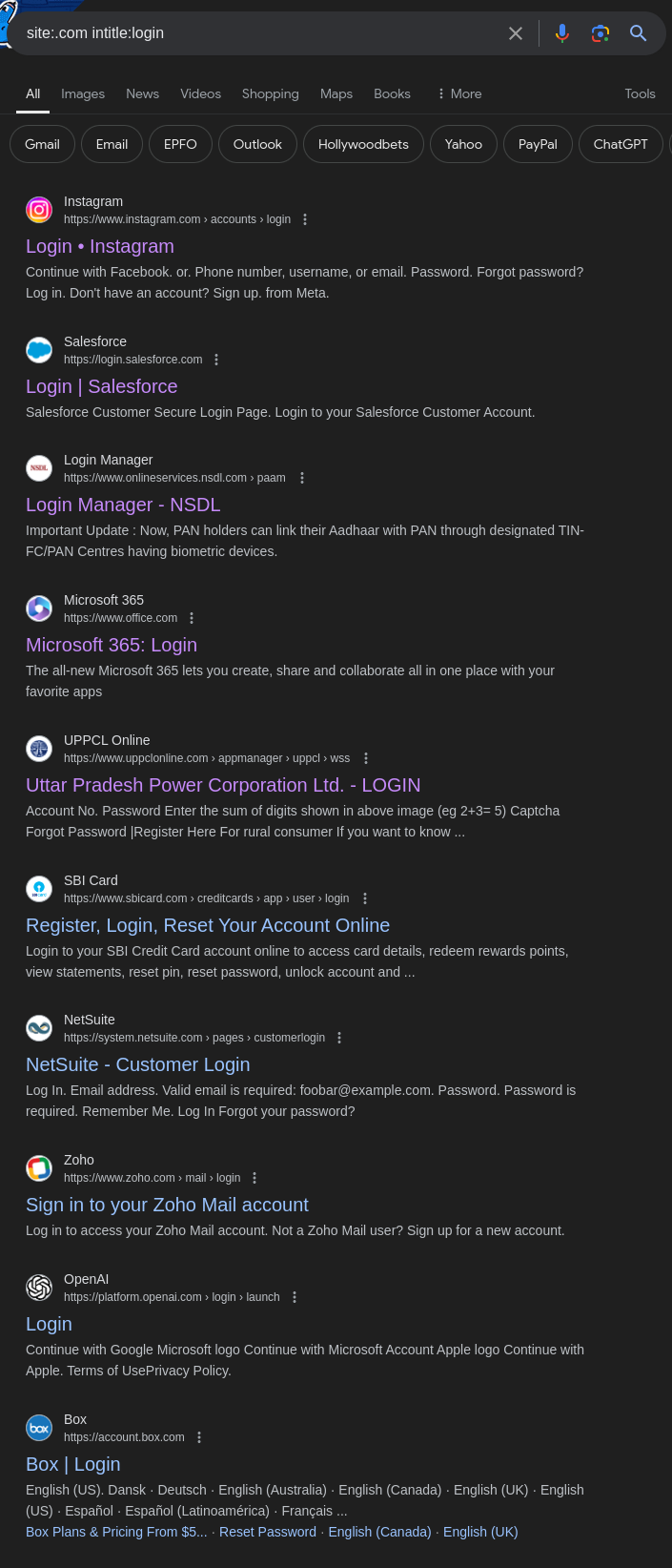
Search results showing pages where “login” appears in the title.
Understanding the Source Code
To see how this works behind the scenes, you can inspect the source code of any webpage by right-clicking and selecting “View Page Source.” Inside the HTML, you’ll find the <title> tag:
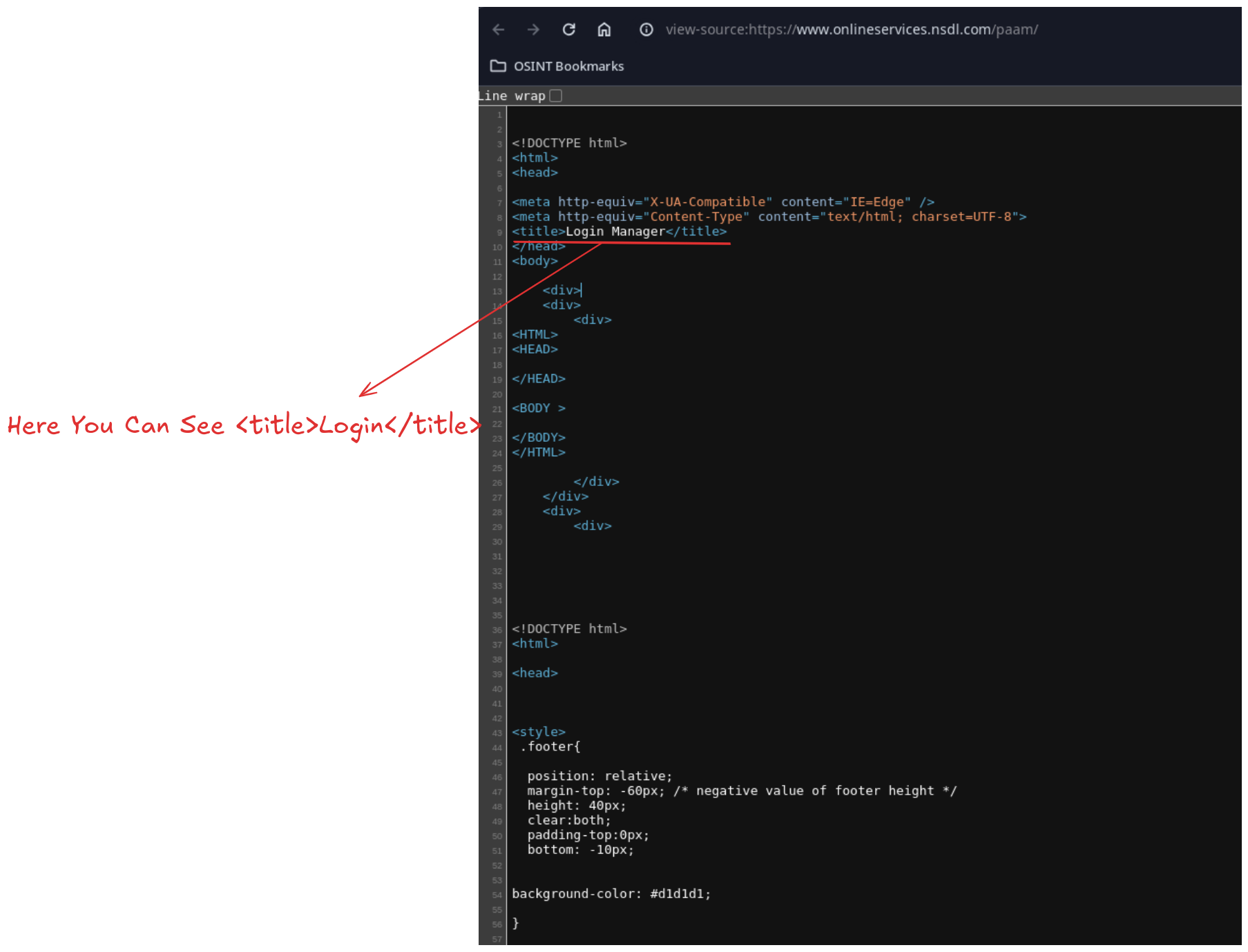
Here, you can see the relevant portion of the code:
1
<title>Login Manager</title>
Because “Login” is in the title of this page, it shows up in your search results using the intitle:login query.
Finding Open Directories
Using the query:
1
site:.com intitle:"index of"
Can help locate directory listings or file directories that might be publicly accessible, revealing potential vulnerabilities or sensitive information.
Example of search results showing pages with “index of” in the title, often indicating open directories.
Potential Uses and Implications
Vulnerabilities: Open directories can expose sensitive files or information unintentionally. This can be a security risk if not properly secured.
SEO Purposes: Sometimes, directory listings are intentionally left open for SEO reasons or to improve site navigation. Webmasters might use such listings to help users find files or resources more easily.
Understanding the context in which these directories are used is important for both security analysis and web development.
Using the address: Operator
The address: operator isn’t a standard search feature in Google, but with Google Dorking, you can use alternative methods and operators to effectively find addresses or locations by combining various operators creatively.
Finding Specific Addresses or Locations
Here are some approaches to uncover addresses or locations using Google Dorking:
Using the site: Operator for Subdomains
If you want to search for address-related information on a specific website or subdomain, you can use the site: operator in combination with relevant keywords. This can be helpful for finding store locations, offices, or other geographic information.
Example: Searching for Tesla Store Addresses
To find stores in the United States on Tesla’s website, you can structure your search like this:
1
site:tesla.com address:stores in united states
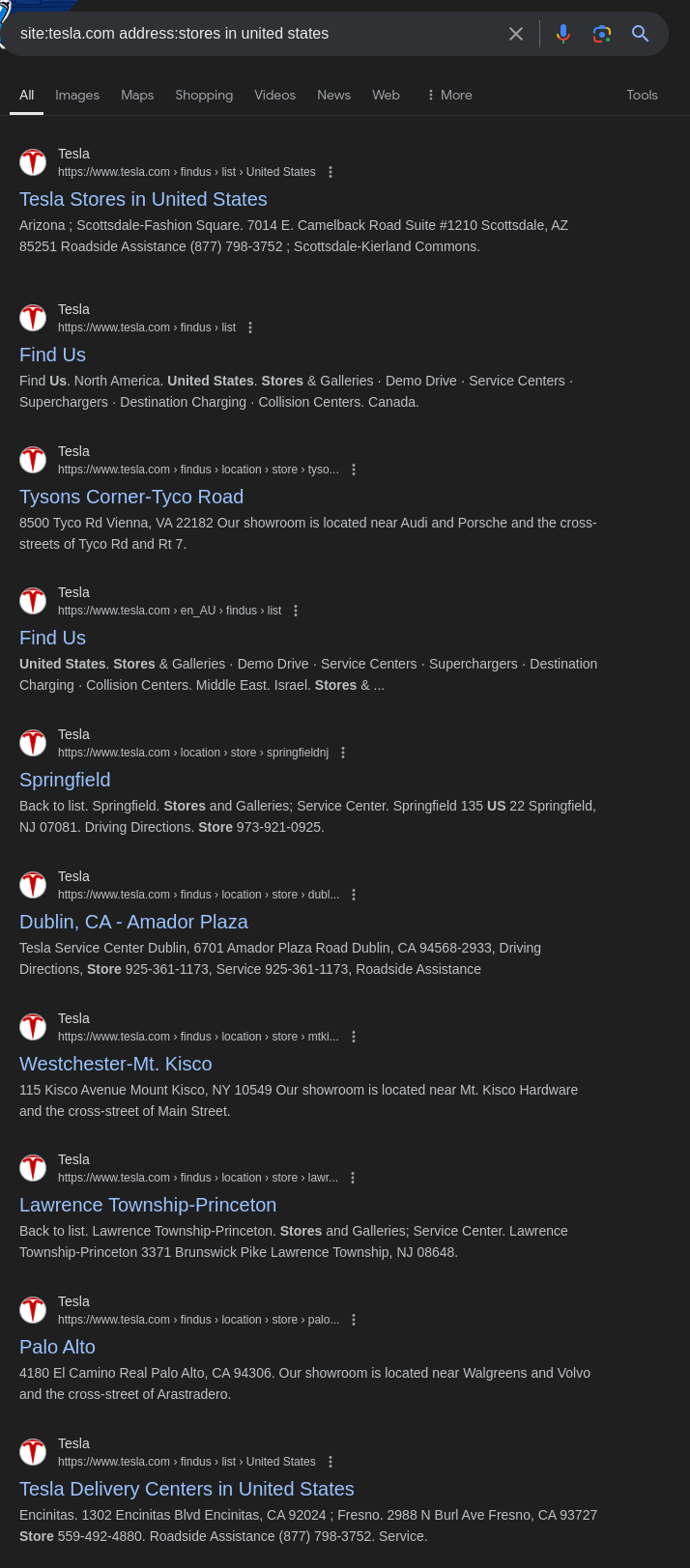 Search results showing Tesla store locations in the United States.
Search results showing Tesla store locations in the United States.
This query focuses on results from tesla.com that mention “address” and “stores” within the United States.
2. Using Google Maps for Address Searches
For more precise location searches, Google Maps can be a more direct tool. You can pair specific location types (like restaurants, shops, or offices) with keywords in a query to narrow down locations.
Example: Searching for Pizza Places in Kerala
You can use the intitle: operator combined with a specific location like this:
1
intitle:pizza address:kerala
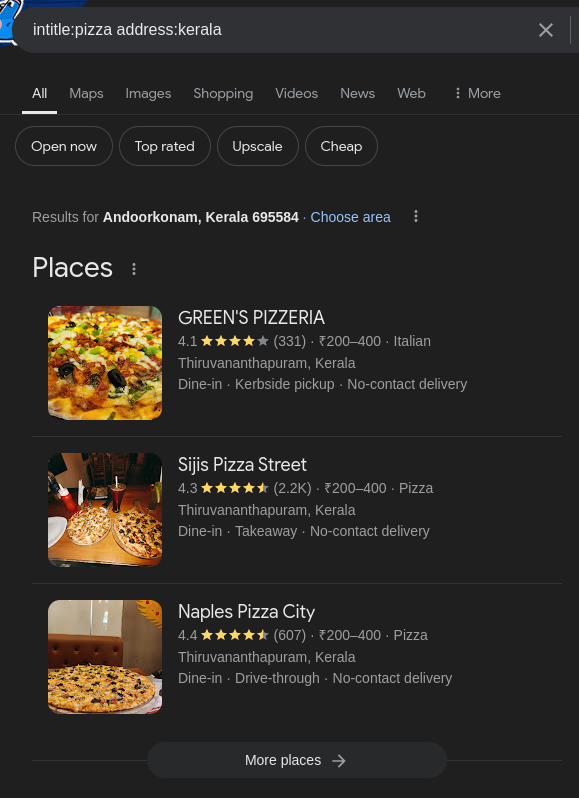 Results showing pizza places with addresses in Kerala.
Results showing pizza places with addresses in Kerala.
This method helps find specific businesses or locations based on the keywords and address details provided.
Even though Google doesn’t have a direct address: operator, combining other operators such as site:, intitle:, and keywords related to addresses can help you locate specific information. Google Maps can also be used as a complementary tool for finding addresses and locations.
Using the intext: Operator
The intext: operator in Google Dorking is used to search for specific words or phrases within the body text of a web page. This operator is particularly useful for finding content where the keyword appears in the text, but not necessarily in the title, URL, or other metadata of the page.
How to Use intext:
To locate pages with a specific keyword or phrase in the content, use this format:
1
intext:keyword
Example:
If you’re searching for pages containing the word “login” within the body text of .com websites, you would use the following query:
1
site:.com intext:login
This query will return pages from .com domains where the word “login” appears in the text of the page.
Similarly, if you want to search for pages containing the word “confidential” within .edu websites, you can use:
1
site:.edu intext:confidential
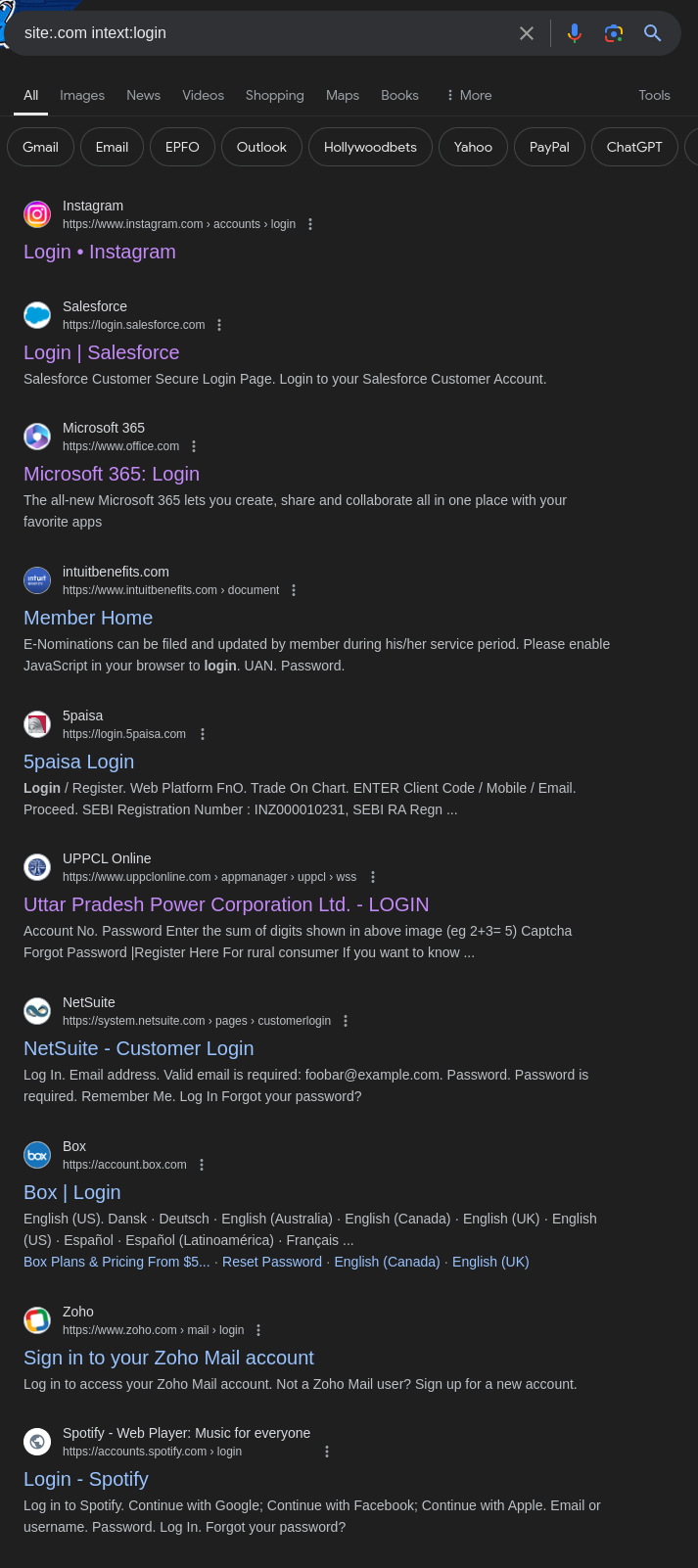
Example results showing pages where “login” or “confidential” appears in the content.
Breakdown:
intext:login— Filters results to show pages where the word login appears in the body text.site:.com— Restricts the search to.comdomains, refining the scope of your search.site:.edu— Restricts the search to.edudomains for academic or educational results.
Use Cases
- Finding Content: The
intext:operator is perfect for locating specific content or keywords within the body of web pages. - Security Research: Useful for identifying pages that reference login or sensitive information, even if the term isn’t in the title or URL.
- Information Gathering: Helps gather content on specific topics from within a large number of pages, especially useful in OSINT (Open-Source Intelligence) investigations.
Using the intext: operator makes it easier to narrow down relevant pages based on the actual content within a page, providing more targeted results for security researchers and information gatherers alike.
Comparing intitle: vs intext: Operators
When performing advanced searches with Google Dorking, knowing how to use the intitle: and intext: operators effectively can greatly improve the precision of your search results. Both operators target different parts of a web page, and understanding their differences is key to refining your queries.
intitle: Operator
- Purpose: Searches for web pages where the specified word or phrase appears in the title of the page.
- Usage: Best for finding pages where the keyword is central to the content and likely to be summarized in the title.
Syntax:
1
intitle:keyword
Example:
1
intitle:login
This query returns web pages where the word “login” appears in the title, such as login portals or login-related articles.
Use Cases:
- Finding Specific Page Types: Ideal for locating pages like login portals, admin panels, or pages centered around specific subjects (e.g., “login” or “admin”).
- High Relevance: Titles are usually written to highlight the main topic of a page, making these results highly relevant to your query.
Example Query: To search for login pages on .com domains:
1
site:.com intitle:login
This query returns results where “login” appears in the title on websites with a .com domain.
intext: Operator
- Purpose: Searches for pages containing the specified word or phrase in the body text of the page.
- Usage: Useful when you need to find pages where the keyword or phrase appears anywhere in the content, even if it’s not the primary focus of the page.
Syntax:
1
intext:keyword
Example:
1
intext:login
This query returns pages where the word “login” appears in the body text, not limited to the title or URL.
Use Cases:
- Broad Content Searches: Helpful for finding pages that discuss a particular keyword within the text, such as explanations or mentions of “login” within a larger article or discussion.
- Comprehensive Search: Unlike
intitle:, the keyword may appear anywhere on the page, so the results cover a wider scope.
Example Query: To find pages discussing login information on .com websites:
1
site:.com intext:login
This query shows pages where “login” appears somewhere in the body text of .com websites.
Summary
intitle:: Targets keywords in the title, giving focused results where the keyword is a central theme or topic of the page.intext:: Targets keywords in the body text, providing broader results where the keyword appears anywhere in the content, even if it’s not the main focus.
Using these operators, either individually or combined, allows for tailored searches. For instance, pairing intitle: with intext: can help locate pages that both discuss a keyword and feature it prominently in the title, offering highly relevant and comprehensive search results.
Using the filetype: Operator
The filetype: operator in Google Dorking is a powerful tool for locating specific types of files on the web by filtering search results to include only files with a particular extension. This operator is valuable for finding various documents, spreadsheets, presentations, and other file types.
How to Use filetype:
To search for files of a specific type, use the following syntax:
1
filetype:extension keyword
extension: The file extension you are targeting (e.g., pdf, docx, xls).keyword: The term or phrase you want to find within those files.
Example Usage
Finding PDF Files:
To locate PDF files related to “cybersecurity”, you would use:
1
filetype:pdf cybersecurity
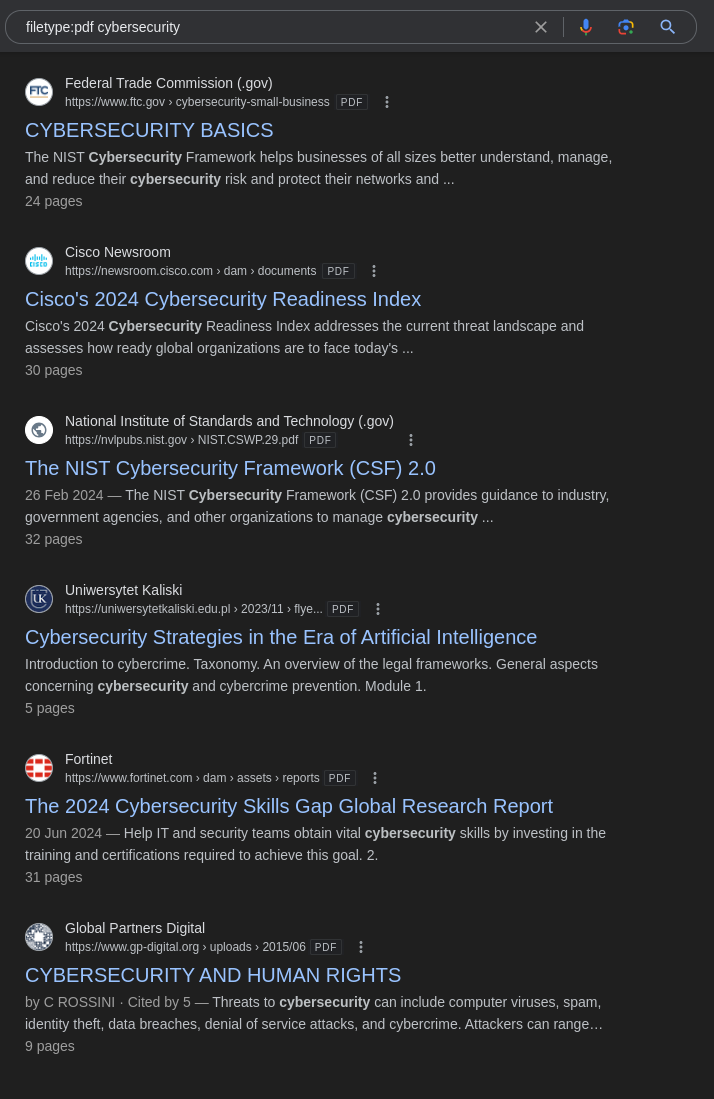
This query returns PDF documents that include the term “cybersecurity”.Finding Word Documents:
To find DOCX files mentioning “project plan”, use:
1
filetype:docx project plan
This will return DOCX files containing the phrase “project plan”.
Finding Excel Spreadsheets:
To search for Excel files related to “financial reports”, use:
1
filetype:xls financial reports
This query displays Excel spreadsheets that mention “financial reports”.
Finding CSV Files:
For discovering CSV files that might contain data, use:
1
filetype:csv data
Many sites store data in CSV format, so this query can help find potentially sensitive information.
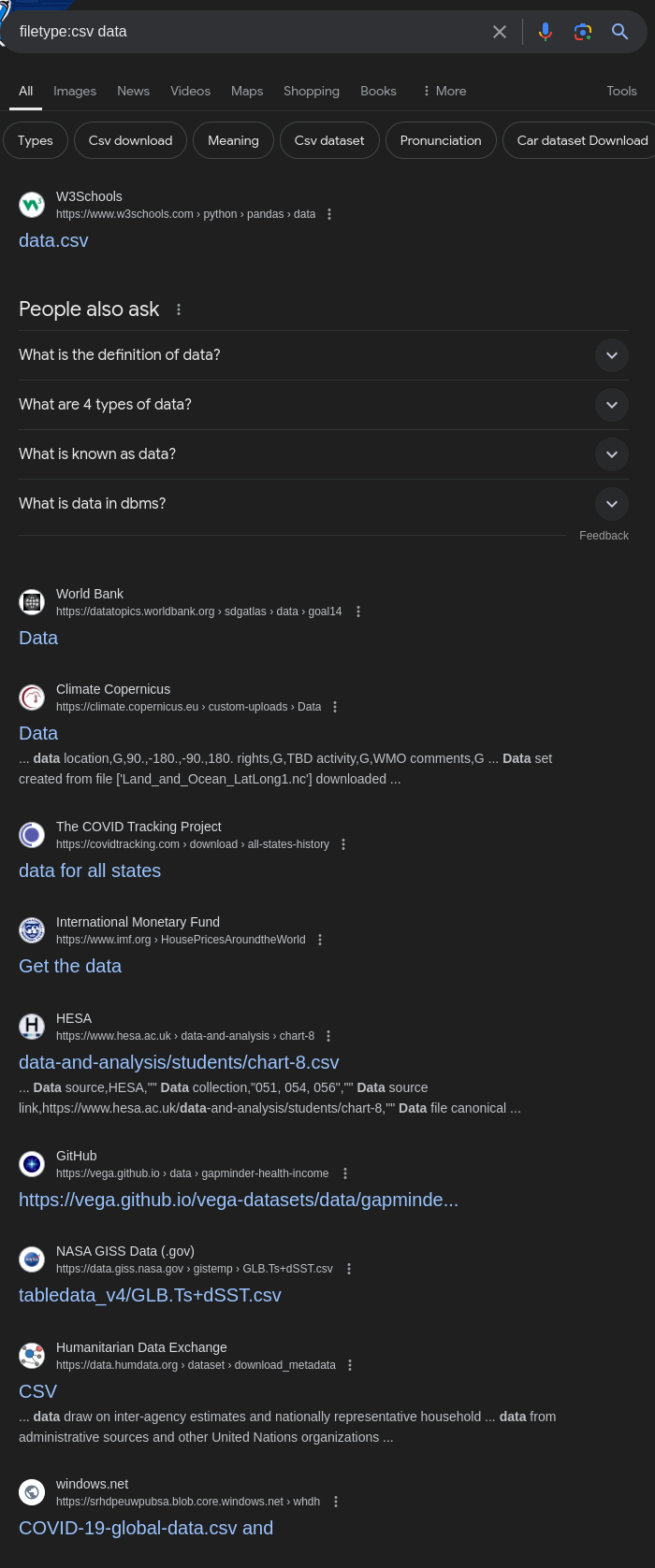
This query can uncover CSV files that may contain valuable or sensitive data.
How It Works
filetype:Operator: Filters search results to include files with a specified extension.- Keyword: The term or phrase that should appear in the content of the files.
Use Cases
- Finding Specific Documents: Ideal for locating particular types of documents, such as technical reports, academic papers, or business plans.
- Research and Data Gathering: Useful for accessing detailed information or datasets often stored in formats like PDF, DOCX, or XLS.
- Security and Vulnerability Assessment: Helps identify exposed documents or files that might contain sensitive or confidential information.
Using the filetype: operator can streamline your search for specific types of files, making it easier to gather information or assess vulnerabilities based on file contents available on the web.
Using the link: Operator
The link: operator in Google search is used to find web pages that contain links to a specific URL or domain. This operator can be quite useful for identifying which sites are linking back to a particular page, making it valuable for tasks like backlink analysis and competitive research.
How to Use link:
To search for pages that link to a particular URL or domain, use the following format:
Example Usage
Finding Links to Tesla on Specific Domains:
To find pages that link to Tesla and are hosted on a
.indomain, you can use:1
link:tesla.com site:.in
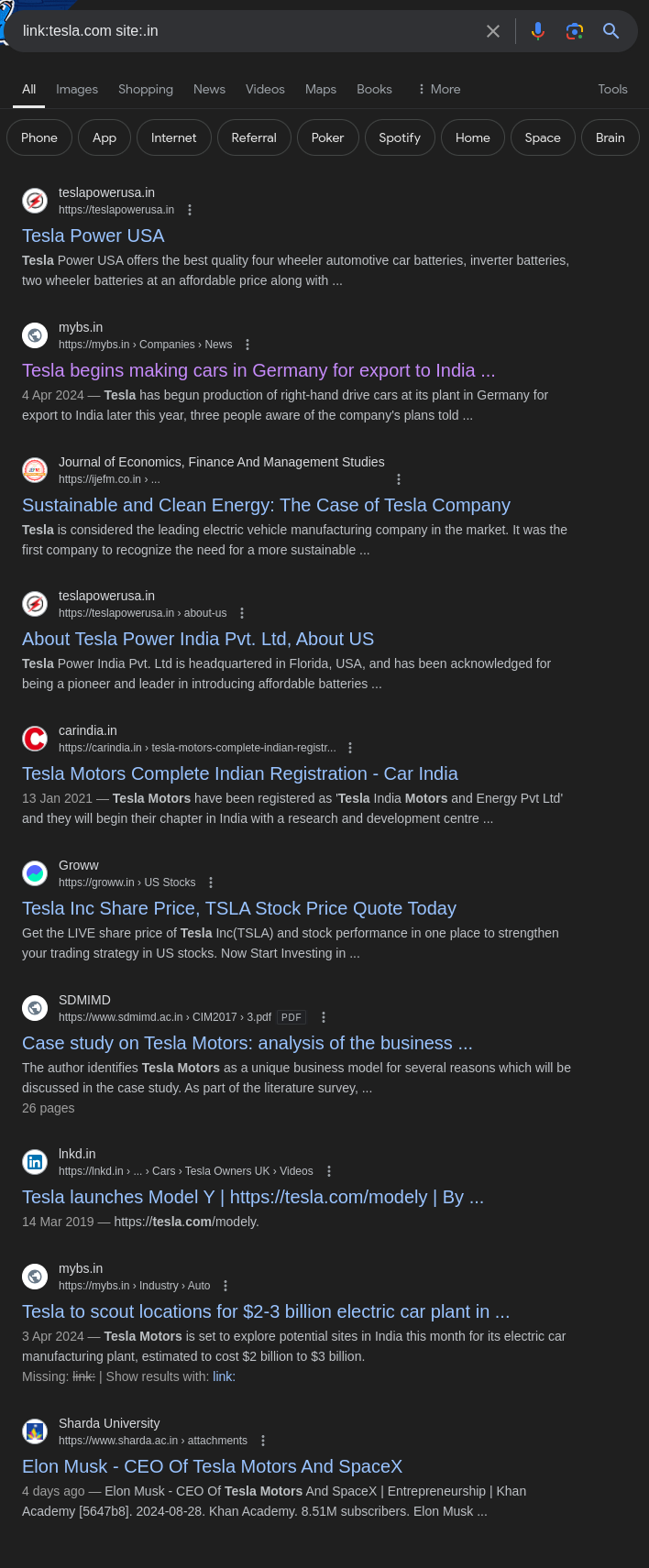 This query returns pages on
This query returns pages on .indomains that contain links to tesla.com.Finding Bug Bounty Reports:
To locate bug bounty reports or discussions related to Tesla on Bugcrowd, use:
1
link:tesla.com site:bugcrowd.com
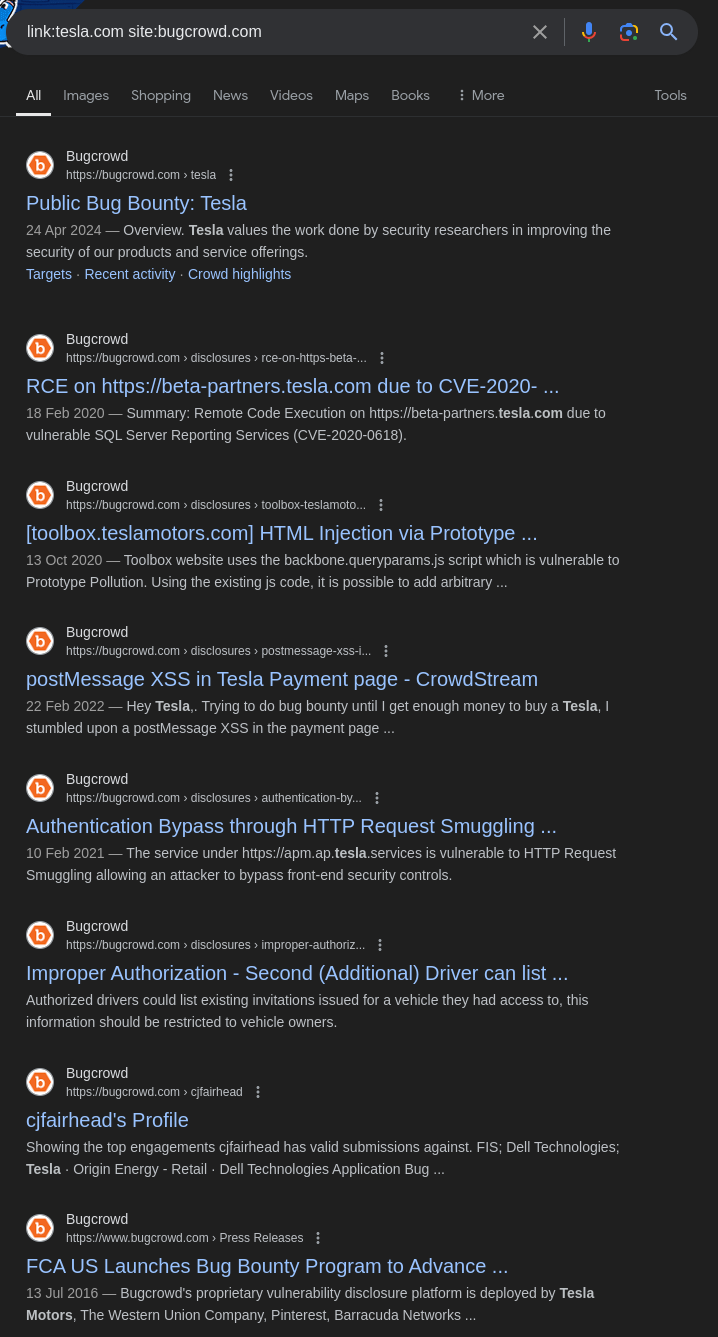
This query identifies pages on Bugcrowd that reference or link to Tesla’s domain, helping you discover relevant bug reports or discussions.
How It Works
link:Operator: Searches for web pages that include links to the specified URL or domain.site:Operator: Allows you to restrict the search to pages within a specific domain or domain type (e.g.,.in,bugcrowd.com).
Use Cases
- SEO and Backlink Analysis: Useful for SEO professionals to identify backlinks to their website, providing insights into which domains are linking to their content and helping to assess the website’s authority.
- Competitive Research: Helps in analyzing backlinks to competitors’ sites, which can reveal their link-building strategies and areas where you might gain a competitive edge.
- Discovering References: Valuable for tracking which pages reference or cite a specific page, helping to measure the influence and reach of content.
- Bug Bounty Reconnaissance: Assists in finding bug bounty reports or discussions related to a target domain on platforms like Bugcrowd, facilitating research and vulnerability discovery.
Limitations
- Inconsistent Results: Google’s results may not be exhaustive. The
link:operator might not return all relevant pages or provide a complete picture of backlinks. - Operator Deprecation: The effectiveness of the
link:operator has diminished over time, with Google reducing its functionality and coverage compared to its earlier capabilities.
By leveraging the link: operator, you can gain valuable insights into backlinks and references, although it’s important to be aware of its limitations and complement it with other tools and techniques for comprehensive analysis.
Using the inurl: Operator
The inurl: operator in Google Dorking is a powerful tool for searching pages that contain a specific term within their URL. This operator is particularly useful for discovering pages with certain directory structures, admin panels, or login pages.
Purpose
- Searches for Pages with Specific Terms in the URL: Helps find web pages where a particular term appears in the URL.
Syntax
To use the inurl: operator, use the following format:
1
inurl:keyword
Example Usage
Finding Admin Panels:
To locate pages that likely contain admin panels by searching for URLs with the term “admin”, use:
1
inurl:admin
Result:
This query will return pages where “admin” appears in the URL, such asexample.com/adminorexample.com/wp-admin. This can help identify administrative interfaces that might be accessible.Finding Login Pages:
To locate login pages by searching for URLs with the term “login”, use:
1
inurl:login
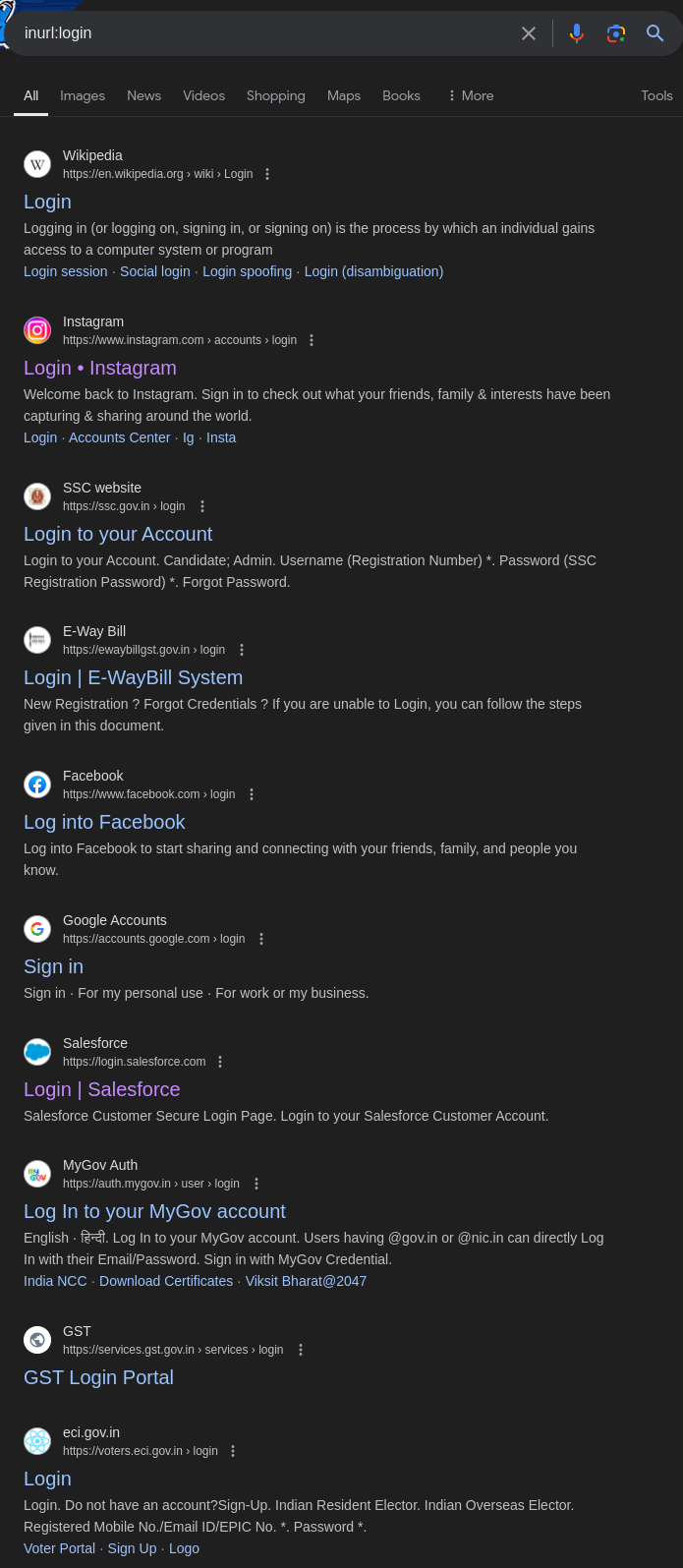
This query returns pages with “login” in the URL, such asexample.com/loginorexample.com/user-login. This is useful for locating authentication pages.
Use Cases
- Finding Admin Panels: Useful for locating administrative interfaces of websites, which can be crucial for security assessments or research.
- Discovering Login Pages: Helps in identifying login pages across various websites, beneficial for penetration testing or vulnerability assessments.
- Locating Specific Directories: Useful for finding pages related to particular directory structures or file management.
Summary
inurl:Operator: Focuses on finding pages that include a specific term within their URL, making it effective for locating pages related to admin interfaces, login pages, or specific directories.
Using the inurl: operator allows you to efficiently identify URLs that contain particular keywords, aiding in security assessments, information gathering, and research.
Here is a table with 50 Google Dorking operators and their descriptions along with example usage:
| Operator | Description | Example |
|---|---|---|
cache: | Shows Google’s cached version of a page | cache:nytimes.com |
related: | Finds websites related to a specific domain | related:bbc.com |
- (exclude) | Excludes results containing a specific word | tesla -model 3 |
OR | Finds pages containing either of two terms | security OR cybersecurity |
* (wildcard) | Replaces unknown or variable words in a search phrase | "cybersecurity * challenges" |
allintitle: | Searches for multiple words in the title | allintitle:cybersecurity attack |
allinurl: | Searches for multiple words in the URL | allinurl:admin login |
allintext: | Searches for multiple words in the body text | allintext:password confidential |
around(x) | Finds words near each other within “x” words | cybersecurity AROUND(5) attack |
define: | Displays the definition of a word | define:hacking |
numrange: | Searches within a range of numbers | laptops $500..$1000 |
before: | Finds pages published before a specific year | cybersecurity before:2015 |
after: | Finds pages published after a specific year | AI after:2020 |
author: | Finds posts or articles by a specific author | author:john_doe |
daterange: | Finds results within a specific date range (Julian dates) | daterange:2459101-2459151 |
info: | Provides information about a website | info:wikipedia.org |
inanchor: | Searches for words in the anchor text of links | inanchor:buy books |
location: | Filters news results by a specific location | location:New York |
stocks: | Provides stock information about a company | stocks:AAPL |
source: | Searches within a specific news source | source:bbc.com |
ext: | Similar to filetype:, searches for file extensions | ext:doc confidential |
map: | Finds maps related to the query | map:Paris |
weather: | Displays weather results for a location | weather:London |
movie: | Shows movie listings or info for a location | movie:New York |
phonebook: | Searches for phone numbers (less effective now) | phonebook:John Doe |
bphonebook: | Searches for business phone numbers | bphonebook:plumber |
rphonebook: | Searches for residential phone numbers | rphonebook:Jane Doe |
safesearch: | Forces safe search for results | safesearch:hacking |
insubject: | Finds words in the subject of a webpage | insubject:AI future |
sitemap: | Finds sitemap pages for a website | sitemap:wikipedia.org |
group: | Restricts search to a particular Google Group | group:rec.humor.funny |
cache-date: | Finds cached versions of a page from a specific date | cache-date:2022-07-15 example.com |
isbn: | Searches for books using their ISBN | isbn:9780134685991 |
inmeta: | Searches in the metadata of a page | inmeta:author name |
insubject: | Searches for words in the subject (useful in Google Groups) | insubject:cybersecurity |
inbook: | Finds references within books on Google Books | inbook:machine learning |
inposttitle: | Searches for words in blog post titles | inposttitle:cybersecurity tips |
intags: | Searches for keywords within a site’s meta tags | intags:security |
ip: | Searches for sites hosted on a specific IP address | ip:192.168.1.1 |
book: | Finds books related to a topic or title | book:artificial intelligence |
place: | Finds places related to the query | place:restaurants |
maps: | Displays results related to maps for a location | maps:Berlin |
patents: | Searches for patents related to the query | patents:renewable energy |
news: | Filters search results to show only news articles | news:cybersecurity |
Additional Resources
For more examples and comprehensive lists of Google dorks, you can explore the following resource:
This GitHub repository contains a collection of Google dorks and search techniques useful for various purposes, including information gathering, security assessments, and more. It’s a valuable resource for anyone looking to expand their knowledge and use of advanced search queries.
Bug Bounty Using Google Dorking
Google Dorking can be a powerful tool for bug bounty hunters, helping to uncover hidden or sensitive information that may be inadvertently exposed online. By crafting specific search queries, you can identify vulnerable systems, exposed data, or misconfigured pages. Here’s how you can use Google Dorking effectively for bug bounty reconnaissance.
Finding Apache2 Default Pages
Default pages from Apache2 installations are often targeted by bug bounty hunters because they can reveal misconfigurations or unprotected systems. Here’s how to use Google Dorking to locate these pages:
Basic Search:
Start with a straightforward query to find default Apache2 pages:
1
intitle:Apache2 Debian Default Page
This search targets pages with “Apache2 Debian Default Page” in the title, which is a common default page for Apache2 installations on Debian systems.
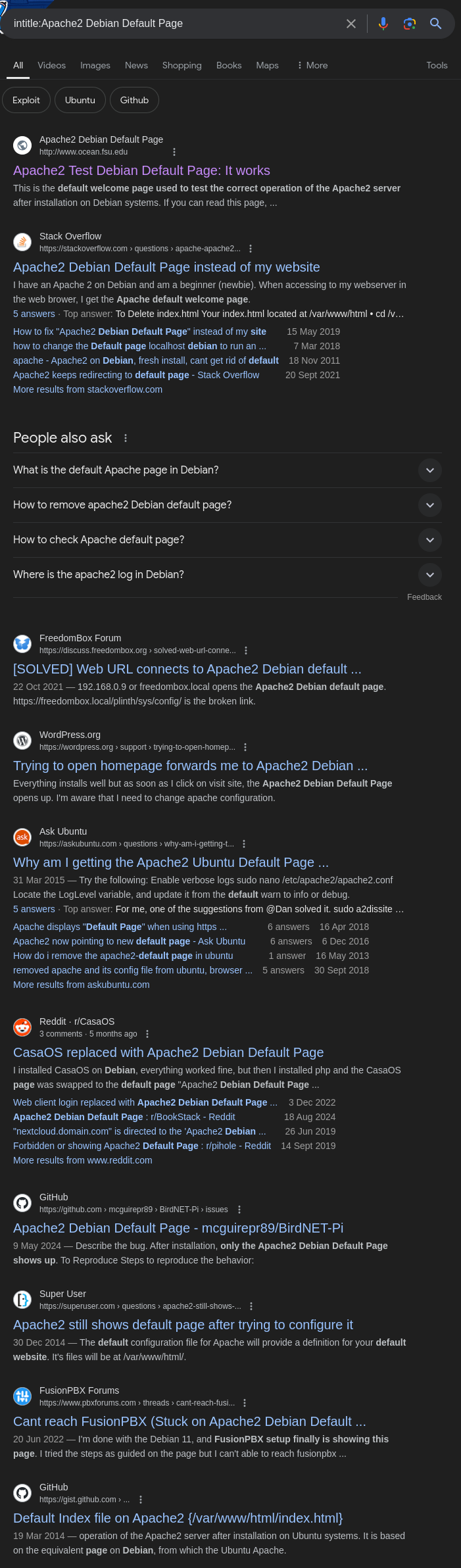
Search results showing pages with the default Apache2 title.Refining with Quotation Marks:
If the basic search results are limited, refine your query by using quotation marks to ensure an exact match for the phrase:
1
intitle:"Apache2 Debian Default Page"
Quotation marks help Google find pages with the exact title, which can yield more comprehensive results.
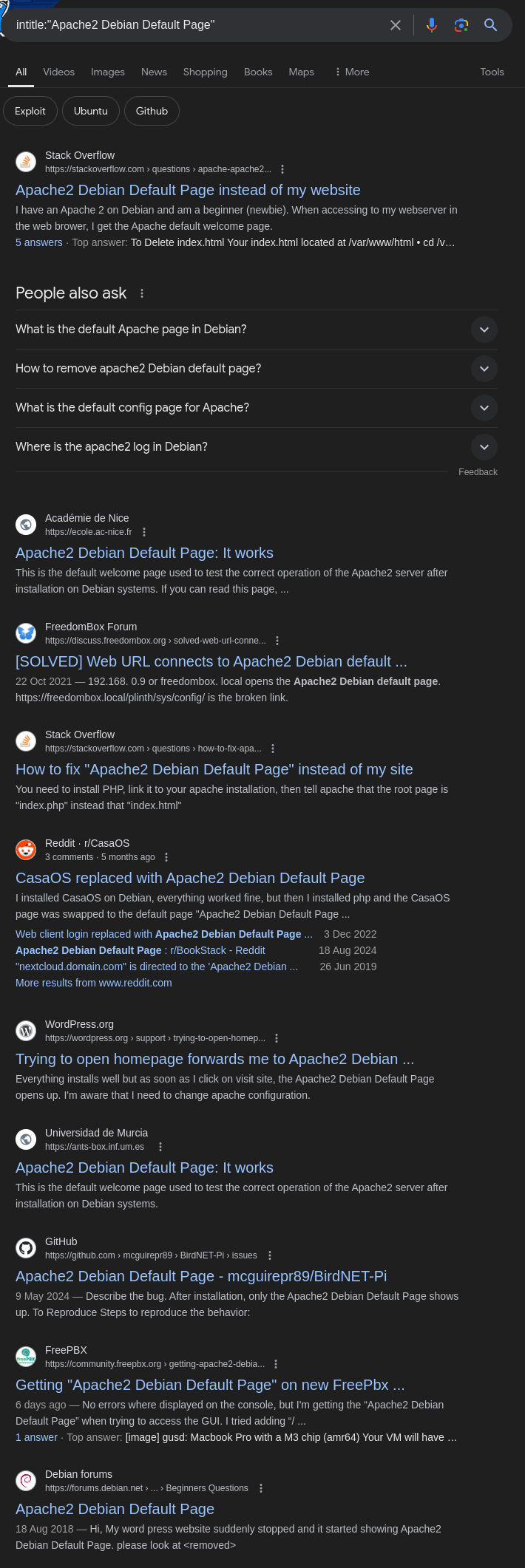
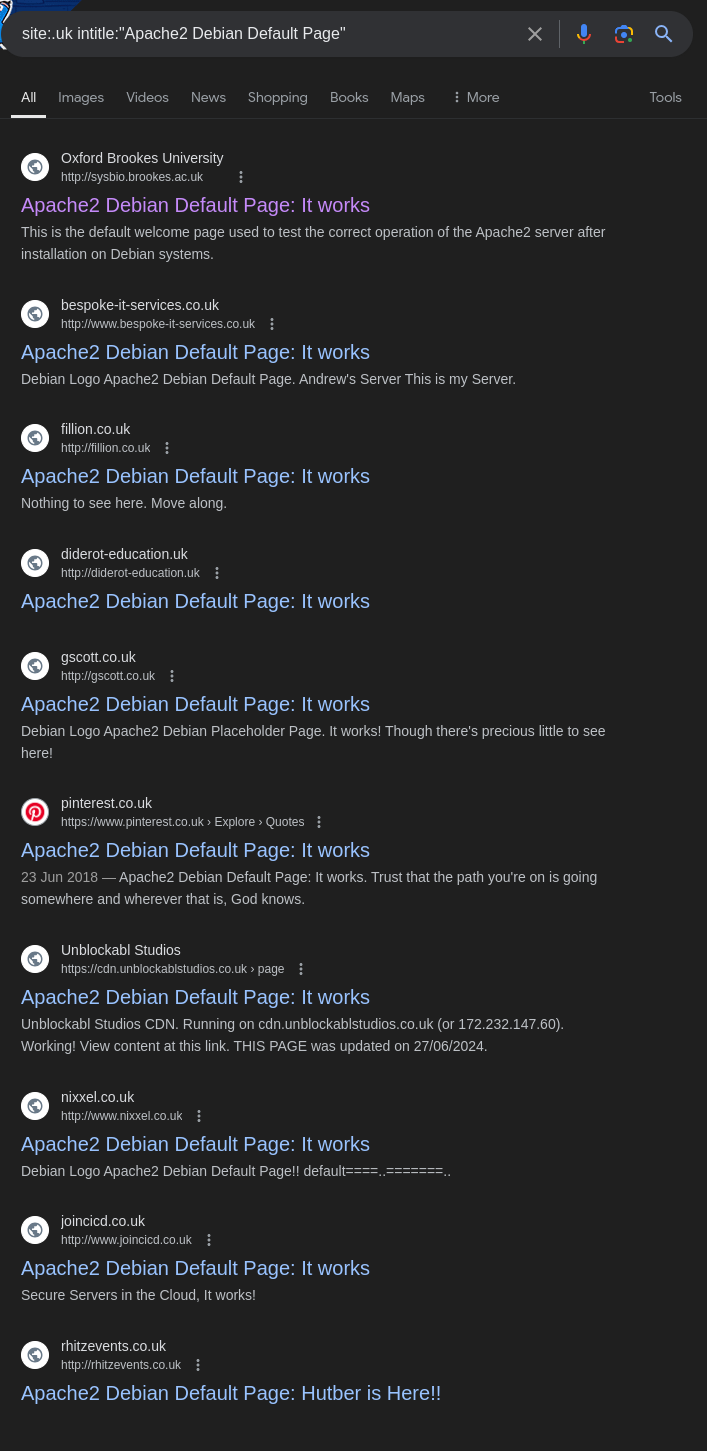
Refined search results displaying the exact match for the title.Targeting Specific Domains:
To narrow down the search to pages within a particular domain or country code top-level domain (ccTLD), use the
site:operator. For example, to find pages within the.ukdomain:1
site:.uk intitle:"Apache2 Debian Default Page"
This query filters results to
.ukdomains, which can be useful for targeting specific geographic regions.
Country Code Top-Level Domains (ccTLDs)
For more targeted searches, you can use country-specific top-level domains (ccTLDs). Here’s a link to a comprehensive list of ccTLDs: Wikipedia’s Country Code Top-Level Domain List.
Finding Exposed Git Files (Directory Listing)
Exposed Git files or repositories can be a significant security risk, as they may reveal source code, configuration files, or other sensitive information. Google Dorking can help you locate these exposed Git directories by searching for specific directory listings.
Search Query
To find exposed Git files or repositories through directory listings, use the following query:
1
intitle:"index of" inurl:.git
Explanation
intitle:"index of": Searches for pages with “index of” in the title, which is commonly associated with directory listings on web servers.inurl:.git: Filters results to URLs containing “.git,” which often indicates the presence of Git repositories.
Example Result
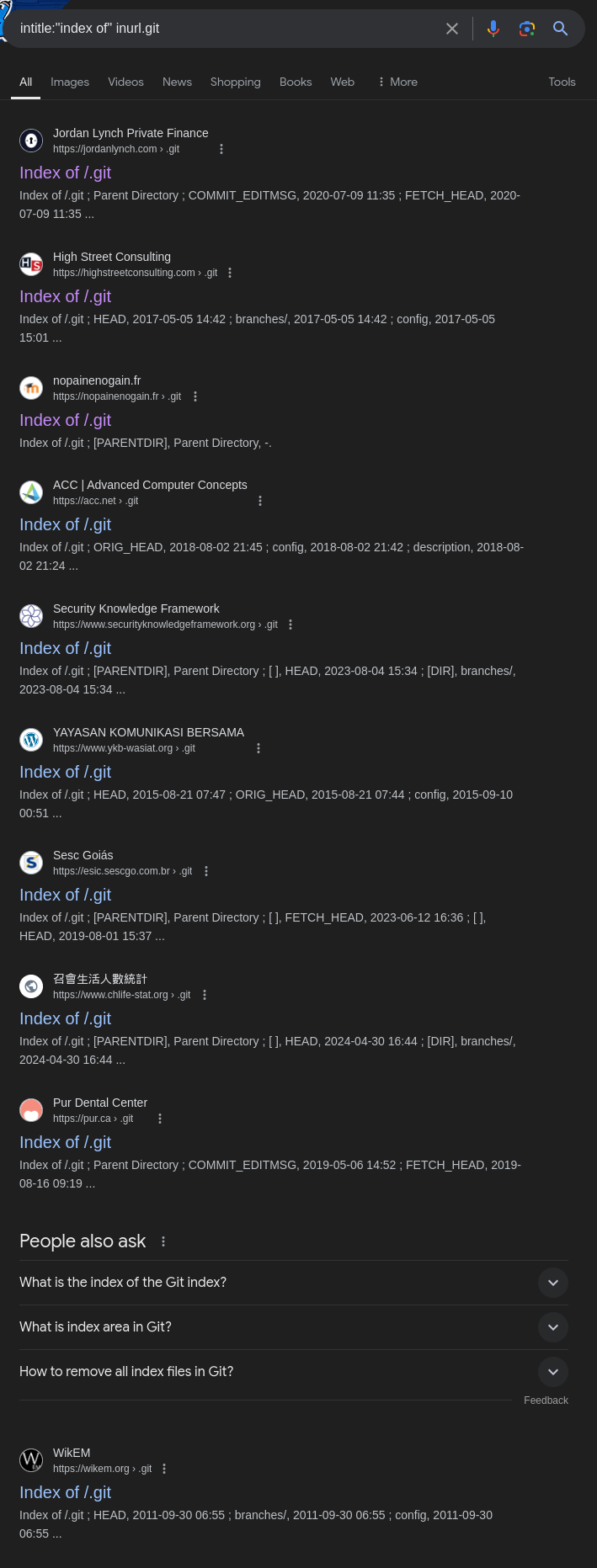
Search results showing exposed Git directories with “index of” in the title.
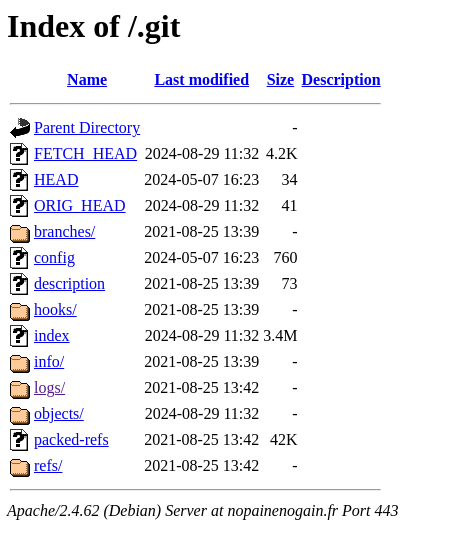 Example of a directory listing page revealing exposed Git files.
Example of a directory listing page revealing exposed Git files.
Finding Configuration Files
For discovering exposed configuration files, you can use a similar approach. For example:
1
intitle:"index of" inurl:config
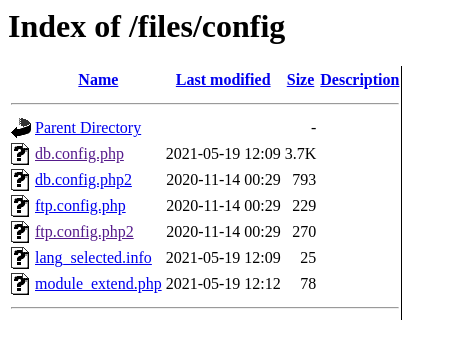
Example of finding sensitive information like FTP configuration files with usernames and passwords, as well as database files.
Use Cases
- Security Assessment: Identifying exposed Git directories can help in assessing the security posture of a target and discovering potentially sensitive files.
- Reconnaissance: Useful for gathering information about a target’s codebase or configuration, which might be inadvertently exposed.
- Vulnerability Research: Helps in finding vulnerabilities that may be present in publicly accessible Git repositories.